So simple, even the CEO can do it
Once upon a time, I used to be able to do useful things. As a CEO I have now forgotten how to do anything useful, except asking other people who still know how to do useful things, to do them.
I was recently reminded that I used to know a bit about hacking. So, when I discovered that a password of mine that I thought was reasonably secure (10 character, uppercase, lower case and special characters) had been breached super quickly I decided I needed to take myself back to school. I learnt password cracking about 15 years ago and the highlight of that experience was cracking the common local admin password of a big defence contractor. It took nearly two weeks and used an embarrassingly large amount of electricity. There are better ways of heating your house, though few that are so satisfying.
When I broke that first password it was done by ‘brute-force’. A process where you essentially try every possible password to see if it works. Computers are pretty good at this. In 2005 my PC could try about 5,000,000 passwords combinations a second. Seems like a lot but a 10 character complex password like my recently broken one could have approximately 60,000,000,000,000,000,000 combinations.
In the last 15 years things have changed. PCs have got much more powerful and you don’t use your CPU to crack passwords any more, but rather a graphics card which is much, much faster. I can now get 840,000,000 tries a second using not very special hardware. But even at that speed, with so many combinations, it’s long hard work to try every combination. And this is where my eureka moment came. You don’t have to try every possibility, because like almost every human being, I am flawed and utterly useless at remembering random passwords. Any reasonably short and memorable password has probably already been cracked and the result published. You can just look it up! Try and make it more difficult with an initial capital letter, so does everyone else. Add some numbers at the end? Yes, everyone else does that too. Going to add a special character. Don’t use a _ or a – because they are the most common.
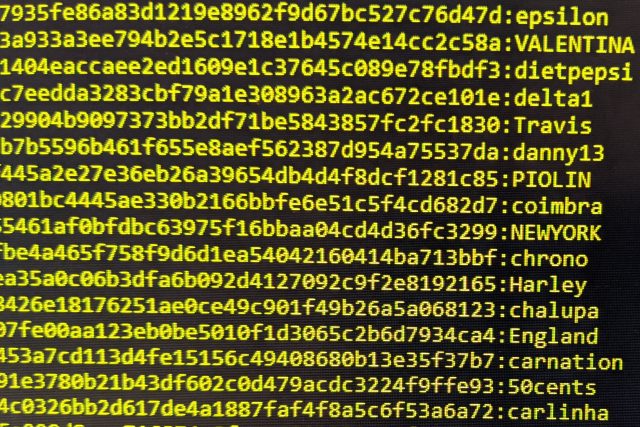
If you can remember it, it’s probably useless. A few days ago I sat down with a list of 1 billion of the most common passwords that I found on the internet. Then I took half a million encrypted passwords from LinkedIn (that were leaked in 2016) and asked my computer to try the combinations from my passwords list against the encrypted passwords. It took about 10 minutes. Not to break one of them, but to break all of them. This isn’t really a surprise because passwords from a breach as big and well-known LinkedIn are likely to already be in the public domain and thus on my list of common passwords.
Passwords suck, but people suck more. In 2018 the most commonly used password was 123456. In 2013 it was 123456. We don’t learn. 4% of all passwords are still 123456 where complexity or length aren’t enforced.
What if you have a great, complex, long and frankly amazing password? Its only any good if you don’t share it. A 2015 study by Intel found that only 65% of people could identify malicious ‘phishing’ emails designed to capture their personal data. Only 3% of people in the study identified all 10 of the test emails. That great, complex, long and frankly amazing password you had – you just gave it away. And now it’s on the internet for everyone to see. Just like mine.
We don’t need to invent a better password; we need to invent a better human.
Giles Letheren – Chief Executive Officer